|
Hacker protection |

|

|
|
|
Hacker protection |

|

|
Hacker protection
The integrated hacker protection serves as a protection against internal attacks additionally to the high encryption. The hacker protection can be configured under edit -> server options -> hacker protection. The more options have been selected, the harder the intervention will be in case of a recognized attempt. If for example all options are activated, a logbook entry will be created at a hacker suspicion, the computer and user will be locked, an email will be sent and additionally the server service will be stopped.
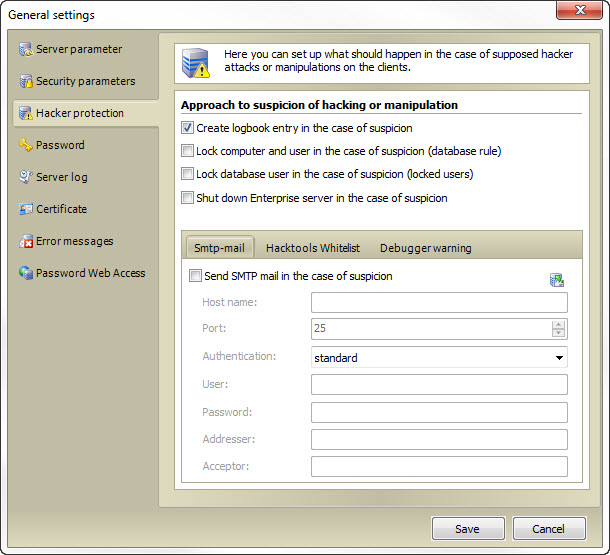
Create logbook entry in case of suspicion: This option causes that all information for the recognized Hacking Tool will be listed in the logbook
Lock computer and user in the case of suspicion (databse rule): With this option, the computer on which the tool was found, as well as the corresponding user is blocked by the firewall. To unlock the firewall rule must be deleted or changed.
Lock database user in the case of suspicion (locked users): This option prevents the user can login. To unlock, open the database overview and right-click the appropriate database. Then you can unlock the user via the menu locked users.
Shut down Enterprise server in the case of suspicion: Beyond this point you can stop the Server service in a suspected hacking can.
You have the opportunity to send in a hacking suspicion an email (for example, the Administrator). Under the tab SMTP mail, you can configure the email account to be used for this purpose.
With a click on ![]() , you can test the settings.
, you can test the settings.
If you use programs that are recognized by Password Safe as HackTool, so you can exclude them on the whitelist from the review. If the option Create logbook entry in case of suspicion is activated, you will find all the information in the logbook. This could look like this:

To exclude the programm (in this case the PowerHex Editior) just copy the infoline from the logbook into the Hacktool Whitelist:

With this entry, the previously Detected tool is excluded from the analysis. You have also the possibility to use RegEx in the whitelist. The following entry means that all tools which begin with "PowerHEX", are passed over in the test routine:
